Social Media Hacking Speaks
For most of the people who's been using the internet from the last 20 years or so the internet, crimes are not a new concept for them. after all, in the field of businesses, organizations, or individuals there are thousands of cases reported in every hour in the world.
Evenly, Right now many people can recognize an email 'hack' and know to avoid it. but a social media hacking world, now that's a new beast.
Hacking Attacks
In the last few years, there have been many social media breaches in the past. From LinkedIn’s 2012 attack that exposes email addresses four years later in 2016, to Facebook's major breach in early 2018, also in 2018 when Instagram users were locked out of their account...in recent attacks in early 2020 when Facebook hack,Social Network Confirms 13.4 Million Follower Twitter Account Compromised, And the most fascinating one twitter hacked in which more than 130 accounts got hijacked including the former president of Barack Obama, Bill Gates, Jeff Bezos, Elon Musk and more.
If you wanna know more about hacks, here;'s a list of some of the top Social Media Hacks that happened in the past few years. Also, there are so many smaller hacks happening that steal 44 records per second.
In particular, According to Statista.com, More than 80% of the US population has at least one social media account. With that sort of reach, and that number likely to continue growing, it's no surprise that computer criminals have found a new playground to cause terrible damage.
Hackers Work
Computer hackers are unauthorized users who forced entry computer systems so as to steal, change, or destroy information, often by installing dangerous malware without your knowledge or permission. Right Now hackers are quite smart.
Hacker are hiding their attacks within social media posts. This exactly happens in the 2017 pentagon attack. One worker clicked on a Twitter Link that advertised a family-friendly vacation, and in one fell swoop, Russian hackers had access to a Pentagon Official's computer.
Why Social Media Is the Main Target
As written by Sheera Frenkel from an equivalent New York Times article as the Pentagon hack above, "the human error that causes people to click on a link sent to them in an email is (more and more as time goes on) greater on social media places...because people more likely think about/believe themselves among friends."
By having a scam where people don't expect it, they are less aware of a possible attack, so they don't see the warning signs. Most people just use their social media to keep up with family and friends and don't see their profiles as valuable information goldmines.
Computer criminals can use your contact list to reach new people, they can use your interests or habits to target email phishing scams, or even see your (looking at web sites on) or shopping history.
Why Hackers Attack
Often times people think, why would anyone want to attack me? the explanations for why hackers hack can vary greatly, from ransoms to easily getting revenge on someone who made them mad.
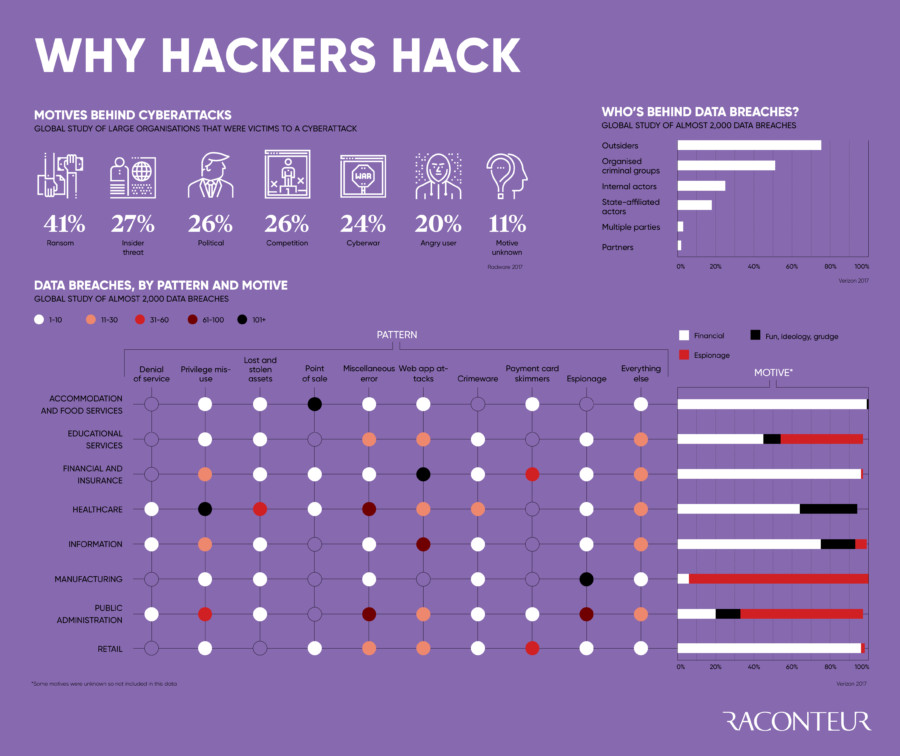
You can check this inforgraphics from raconteur.net
Why you ought to Secure Your Accounts
While your Instagram profile crammed with pictures of your adorable dog could seem innocent enough, protecting your data and online identity with a secure password can prevent a not-so-cute social media attack. Creating unique and secure passwords is that the best thanks to secure your accounts.
we all know it's tons to stay track of, but if you would like your social media and other accounts as secure as possible, use a special password for each account. That way, if one account is hacked, the others will remain secure. confirm each password features a combination of letters, numbers, and punctuation symbols.
If you’re having trouble arising with a “random” enough password, do an inquiry for online password generators. Another good way to secure your accounts is to enable Two-Factor Authentication wherever possible.


Post a Comment