Apple earlier this year fixed a security vulnerability in iOS and macOS that would have potentially allowed an attacker to realize unauthorized access to a user's iCloud account.
Uncovered in February by Thijs Alkemade, a security specialist at IT security firm Computest, the flaw resided in Apple's implementation of TouchID (or FaceID) biometric feature that authenticated users to log in to websites on Safari, specifically people who use Apple ID logins.
After the difficulty was reported to Apple through their responsible disclosure program, the iPhone maker addressed the vulnerability during a server-side update.
An Authentication Flaw
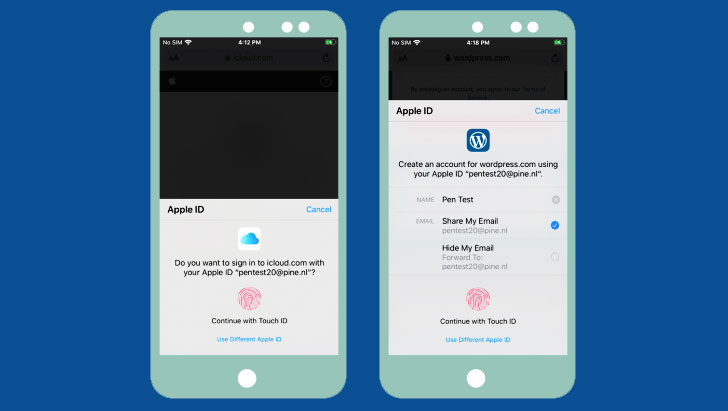
The central premise of the flaw is as follows. When users attempt to check in to an internet site that needs an Apple ID, a prompt is showed authenticate the login using Touch ID. Doing so skips the two-factor authentication step since it already leverages a mixture of things for identification, like the device (something you have) and therefore the biometric information (something you are).
Contrast this during logins to Apple domains (e.g. "icloud.com") the standard way with an ID and password, wherein the web site embeds an iframe pointing to Apple's login validation server ("https://idmsa.apple.com"), which handles the authentication process.
As shown within the video demonstration, the iframe URL also contains two other parameters — a "client_id" identifying the service (e.g., iCloud) and a "redirect_uri" that has the URL to be redirected to after successful verification.
But within the case where a user is validated using TouchID, the iframe is handled differently therein it communicates with the AuthKit daemon (akd) to handle the biometric identification and subsequently retrieve a token ("grant_code") that's employed by the icloud.com page to continue the login process.
To do this, the daemon communicates with an API on "gsa.apple.com," to which it sends the small print of the request and from which it receives the token.
The security flaw discovered by Computest resides within the aforementioned gsa.apple.com API, which made it theoretically possible to abuse those domains to verify a client ID without authentication.
"Even though the client_id and redirect_uri were included within the data submitted thereto by akd, it didn't make sure the redirect URI matches the client ID," Alkemade noted. "Instead, there was only a whitelist applied by AKAppSSOExtension on the domains. All domains ending with apple.com, icloud.com and icloud.com.cn were allowed."
This means that an attacker could exploit a cross-site scripting vulnerability on anybody of Apple's subdomains to run a malicious snippet of JavaScript code which will trigger a login prompt using the iCloud client ID, and use the grant token to get a session on icloud.com.
Setting Up Fake Hotspots to require Over iCloud Accounts
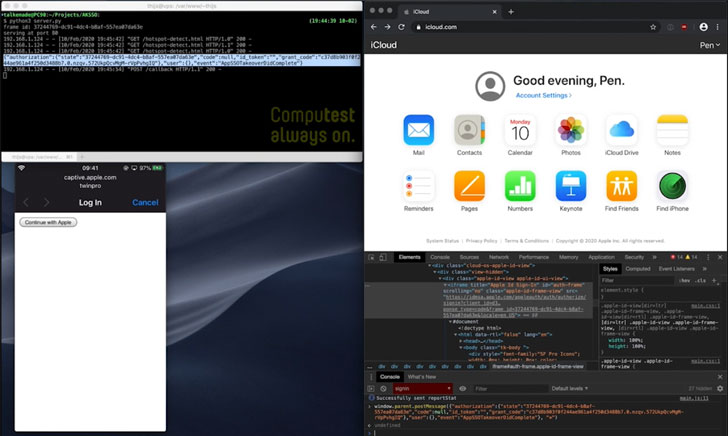
In a separate scenario, the attack might be executed by embedding JavaScript on the online page that's displayed when connecting to a Wi-Fi network for the primary time (via "captive.apple.com"), thus allowing an attacker access to a user's account by just accepting a TouchID prompt from that page.
"A malicious Wi-Fi network could respond with a page with JavaScript which initiates OAuth as iCloud," Alkemade said. "The user receives a TouchID prompt, but it's extremely unclear what it implies. If the user authenticates thereon prompt, their session token are going to be sent to the malicious site, giving the attacker a session for his or her account on iCloud."
"By fixing a fake hotspot during a location where users expect to receive a captive portal (for example at an airport, hotel or train station), it might are possible to realize access to a big number of iCloud accounts, which might have allowed access to backups of images , location of the phone, files and far more," he added.
This is not the primary time security issues are found in Apple's authentication infrastructure. In May, Apple patched a flaw impacting its "Sign in with Apple" system that would have made it possible for remote attackers to bypass authentication and take over targeted users' accounts on third-party services and apps that are registered using Apple's sign-in option.
NEWS SOURCE :THEHACKERNEWS button
Found this text interesting? Follow crimes.me on Facebook, Twitter to read more exclusive content we post.
Uncovered in February by Thijs Alkemade, a security specialist at IT security firm Computest, the flaw resided in Apple's implementation of TouchID (or FaceID) biometric feature that authenticated users to log in to websites on Safari, specifically people who use Apple ID logins.
After the difficulty was reported to Apple through their responsible disclosure program, the iPhone maker addressed the vulnerability during a server-side update.
An Authentication Flaw
The central premise of the flaw is as follows. When users attempt to check in to an internet site that needs an Apple ID, a prompt is showed authenticate the login using Touch ID. Doing so skips the two-factor authentication step since it already leverages a mixture of things for identification, like the device (something you have) and therefore the biometric information (something you are).
Contrast this during logins to Apple domains (e.g. "icloud.com") the standard way with an ID and password, wherein the web site embeds an iframe pointing to Apple's login validation server ("https://idmsa.apple.com"), which handles the authentication process.
As shown within the video demonstration, the iframe URL also contains two other parameters — a "client_id" identifying the service (e.g., iCloud) and a "redirect_uri" that has the URL to be redirected to after successful verification.
But within the case where a user is validated using TouchID, the iframe is handled differently therein it communicates with the AuthKit daemon (akd) to handle the biometric identification and subsequently retrieve a token ("grant_code") that's employed by the icloud.com page to continue the login process.
To do this, the daemon communicates with an API on "gsa.apple.com," to which it sends the small print of the request and from which it receives the token.
The security flaw discovered by Computest resides within the aforementioned gsa.apple.com API, which made it theoretically possible to abuse those domains to verify a client ID without authentication.
"Even though the client_id and redirect_uri were included within the data submitted thereto by akd, it didn't make sure the redirect URI matches the client ID," Alkemade noted. "Instead, there was only a whitelist applied by AKAppSSOExtension on the domains. All domains ending with apple.com, icloud.com and icloud.com.cn were allowed."
This means that an attacker could exploit a cross-site scripting vulnerability on anybody of Apple's subdomains to run a malicious snippet of JavaScript code which will trigger a login prompt using the iCloud client ID, and use the grant token to get a session on icloud.com.
Setting Up Fake Hotspots to require Over iCloud Accounts
In a separate scenario, the attack might be executed by embedding JavaScript on the online page that's displayed when connecting to a Wi-Fi network for the primary time (via "captive.apple.com"), thus allowing an attacker access to a user's account by just accepting a TouchID prompt from that page.
"A malicious Wi-Fi network could respond with a page with JavaScript which initiates OAuth as iCloud," Alkemade said. "The user receives a TouchID prompt, but it's extremely unclear what it implies. If the user authenticates thereon prompt, their session token are going to be sent to the malicious site, giving the attacker a session for his or her account on iCloud."
"By fixing a fake hotspot during a location where users expect to receive a captive portal (for example at an airport, hotel or train station), it might are possible to realize access to a big number of iCloud accounts, which might have allowed access to backups of images , location of the phone, files and far more," he added.
This is not the primary time security issues are found in Apple's authentication infrastructure. In May, Apple patched a flaw impacting its "Sign in with Apple" system that would have made it possible for remote attackers to bypass authentication and take over targeted users' accounts on third-party services and apps that are registered using Apple's sign-in option.
NEWS SOURCE :THEHACKERNEWS button
Found this text interesting? Follow crimes.me on Facebook, Twitter to read more exclusive content we post.


إرسال تعليق